Elevating Healthcare IT: Partnered Solutions IT is Lane County’s Premier IT Medical Provider
Wednesday, 24 January 2024
In the dynamic world of healthcare, where every second counts and precision is paramount, having a reliable IT partner is not just a choice; it’s a strategic imperative. Partnered Solutions IT (PSIT) stands tall as Lane County’s premier medical IT provider, offering a comprehensive suite of services meticulously crafted to meet medical practices, hospitals, and
- Published in Optimize, Secure, Uncategorized
No Comments
Streamlining IT Security for Manufacturers
Thursday, 02 November 2023
In today’s technology-driven world, IT security is a paramount concern for companies across various industries. However, manufacturers face unique IT security challenges that demand specialized solutions. Partnered Solutions IT is dedicated to addressing these specific challenges and enhancing cybersecurity measures for manufacturing companies. With extensive expertise and notable partnerships, they streamline IT security in ways
Elevating Local IT Security: Why Partnered Solutions IT Stands Out
Thursday, 24 August 2023
In today’s fast-paced digital landscape, robust IT security is not just a choice; it’s a necessity. Businesses of all sizes, from small startups to large enterprises, are consistently facing the challenge of safeguarding their sensitive data and ensuring the smooth functioning of their operations. Amidst this complex scenario, having a trusted partner to handle IT
Navigating HIPAA Compliance in Cybersecurity: A Guide for Businesses
Friday, 09 June 2023
In the digital age, cybersecurity is paramount for businesses, particularly in sensitive industries like healthcare. Understanding HIPAA compliance and its role in safeguarding sensitive patient data is crucial. In this SEO-focused blog, we will explore the importance of HIPAA compliance in cybersecurity and provide insights on how businesses can navigate the complex landscape to protect
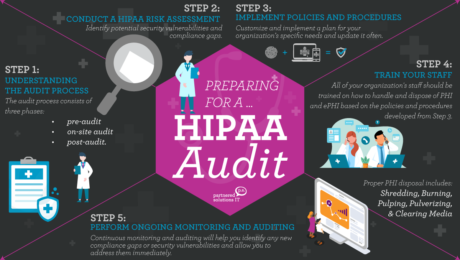
How to Prepare for a HIPAA Audit and Pass With Flying Colors
Thursday, 01 June 2023
As technology continues to play a significant role in the healthcare industry, maintaining compliance with the Health Insurance Portability and Accountability Act (HIPAA) is more critical than ever. Failing to comply with HIPAA regulations can lead to severe financial and reputational damages for medical practices, making it crucial for these organizations to prepare for a
HIPAA Compliance in 2022
Wednesday, 17 November 2021
Are you caught up on HIPAA compliance? Here at Partnered Solutions IT, we are dedicated to making sure you and your practice have all your bases covered when it comes to security compliance. If you want to learn more about HIPAA compliance standards and how to maintain compliance in the new year, read on or
How To Use Zoom Safely: The Big Questions Answered
Wednesday, 08 April 2020
Partnered Solutions’ Chief Security Officer and Chief Operating Officer weigh in on the big questions surrounding the security of the video conferencing tool, Zoom. What makes Zoom such a popular choice over other programs like WebEx, Go To Meeting, or Blue Jeans? The main features of Zoom are ease of use and inter-operability with phones,
- Published in Secure
Tips for Safely Working Remotely
Tuesday, 24 March 2020
We here at Partnered Solutions IT, like many of you, are making adjustments to keep our own staff safe and healthy, working from home. Furthermore, we are also furiously working to keep our clients’ staff working as efficiently as possible. To that end, we have been implementing secure remote work access for our staff and
We are pleased to announce the opening of our Medford office!
Tuesday, 01 October 2019
Nov. 1 Update: The Partnered Solutions IT Medford Office is now open! The rumors are true…Partnered Solutions IT is expanding! From our headquarters almost 10 years ago in a 3-bedroom house, to our current 6,000 square-foot office space in downtown Eugene in 2017, we are ready to make another jump: a satellite office based in
HIPAA Compliance in 2019
Wednesday, 05 June 2019
The Health Insurance Portability and Accountability Act (HIPAA) sets the regulations for sensitive patient data protection for the healthcare industry. Companies that collect, store or use protected health information must have physical, network, and process security measures to keep data safe and be in compliance with HIPAA. Any entity that provides treatment, payment, or operations
- 1
- 2