Future-Proofing Your Medical Office: Leveraging Edge Computing for Enhanced Efficiency
Friday, 28 July 2023
In today’s fast-paced healthcare industry, medical offices face increasing demands for real-time data processing, seamless connectivity, and enhanced efficiency. As patient care becomes increasingly reliant on technology, future-proofing medical offices become a top priority. Edge computing emerges as a transformative solution, offering the potential to revolutionize the way medical data is processed, stored, and utilized.
- Published in Uncategorized
No Comments
Local IT Support vs. Value Added Resellers: Boots-on-the-Ground Matters
Friday, 28 July 2023
In today’s technology-driven world, reliable and efficient IT support is a critical aspect of running a successful medical practice. As medical offices increasingly rely on digital infrastructure and patient data management, choosing the right IT support model becomes paramount. Two primary options for IT support stand out: local IT support and value-added resellers (VARs). While
- Published in Uncategorized
Navigating HIPAA Compliance in Cybersecurity: A Guide for Businesses
Friday, 09 June 2023
In the digital age, cybersecurity is paramount for businesses, particularly in sensitive industries like healthcare. Understanding HIPAA compliance and its role in safeguarding sensitive patient data is crucial. In this SEO-focused blog, we will explore the importance of HIPAA compliance in cybersecurity and provide insights on how businesses can navigate the complex landscape to protect
Local On-Site IT Solutions for Medical Practices
Thursday, 01 June 2023
Ensuring HIPAA compliance and maintaining robust IT security is paramount for medical offices in today’s digital landscape. Partnered Solutions IT, a reputable IT security organization based in Eugene, Oregon, specializes in providing tailored services to medical offices, strongly emphasizing local expertise and on-site support. In this blog, we will delve into the significance of local
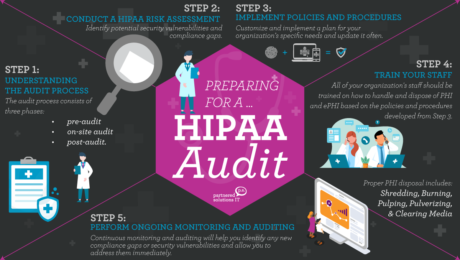
How to Prepare for a HIPAA Audit and Pass With Flying Colors
Thursday, 01 June 2023
As technology continues to play a significant role in the healthcare industry, maintaining compliance with the Health Insurance Portability and Accountability Act (HIPAA) is more critical than ever. Failing to comply with HIPAA regulations can lead to severe financial and reputational damages for medical practices, making it crucial for these organizations to prepare for a
HIPAA Compliance in 2022
Wednesday, 17 November 2021
Are you caught up on HIPAA compliance? Here at Partnered Solutions IT, we are dedicated to making sure you and your practice have all your bases covered when it comes to security compliance. If you want to learn more about HIPAA compliance standards and how to maintain compliance in the new year, read on or
Shopping for an IT Company: The Five Big Questions to Ask
Thursday, 12 November 2020
So you’re shopping for an IT company. Perhaps you have come to the realization you need one, or perhaps you’ve become frustrated with the one you’re working with; in any case, this may be unchartered territory. Some things are no-brainers; you want a team with a depth of skillsets, with different specialists in areas like
- Published in Manage
The basics of cloud-integrated edge computing
Friday, 10 April 2020
Here at Partnered Solutions, we are excited to be rolling out something that we think will revolutionize the way businesses handle IT for the rest of the decade. Yes, that’s right, the decade. We know how fast technology changes and this is a bold statement. So what are the current challenges that we’re addressing? Well,
- Published in Manage
How To Use Zoom Safely: The Big Questions Answered
Wednesday, 08 April 2020
Partnered Solutions’ Chief Security Officer and Chief Operating Officer weigh in on the big questions surrounding the security of the video conferencing tool, Zoom. What makes Zoom such a popular choice over other programs like WebEx, Go To Meeting, or Blue Jeans? The main features of Zoom are ease of use and inter-operability with phones,
- Published in Secure
Tips for Safely Working Remotely
Tuesday, 24 March 2020
We here at Partnered Solutions IT, like many of you, are making adjustments to keep our own staff safe and healthy, working from home. Furthermore, we are also furiously working to keep our clients’ staff working as efficiently as possible. To that end, we have been implementing secure remote work access for our staff and